Pentesting learning path and experience
From Spark to Skill: The Journey to Becoming a Penetration Tester 🔥💻
Starting in 2021, my journey into the realm of penetration testing was sparked by the thrill of learning how to think like a hacker, with ethical intentions, of course. Watching courses by Heath Adams (The Cyber Mentor, TCM Academy) introduced me to the fascinating world of cybersecurity, where pentesters are hired to ethically break into companies, uncover vulnerabilities, and protect assets. But the journey from that initial interest to practical expertise is a multi-layered adventure. Here’s how to level up and avoid the pitfalls along the way.
Building the Foundation: Essential Skills to Master 🛠️
1. Certifications Are Just the Start
- CompTIA A+, Network+, and Security+: Think of these as your foundational triad. They provide you with the language of IT, teach you how networks interact, and introduce essential security concepts. But don’t stop there. These certs open the door, but real-world testing requires deeper, practical application.
- Lab Time Is Non-Negotiable: Hands-on practice is where theory solidifies. Create your own labs, simulate real-world networks, and challenge yourself with unexpected scenarios. Sites like Hack The Box, TryHackMe, and VulnHub are invaluable playgrounds for testing your knowledge.
2. Understanding Operating Systems 🖥️
- Windows and Linux Mastery: These are your bread and butter. Privilege escalation often requires a deep understanding of how processes, services, and security features work within both environments. Dive into concepts like User Account Control (UAC) bypassing and Windows Defender evasion.
- The Windows Active Directory (AD): This is especially crucial. AD environments are a pentester’s challenge and playground. Grasp the fundamentals like Kerberos authentication, TGT and TGS tickets, and how attacks like Pass-the-Ticket and Pass-the-Hash exploit weaknesses.
- Linux Privilege Escalation: Understand SUID/SGID binaries, PATH misconfigurations, and common exploit paths. The more familiar you are with Linux nuances, the faster you’ll identify potential escalation vectors.
3. Basic Scripting and Automation
- PowerShell and Bash: These aren’t just for sysadmins. Basic command-line fluency enables you to script reconnaissance tasks, automate basic operations, and troubleshoot environments more effectively. Knowing how to run scripts to query AD, perform enumeration, and modify configurations can save hours.
- Python: Your universal tool. It’s not just about writing new scripts but understanding the ones you find. Deciphering exploits and tweaking them for specific use cases is a skill that comes in handy during assessments.
Mastering Web Application Hacking 🌐
Penetration testing extends beyond network pentesting; web applications are a rich target:
- PortSwigger’s Web Security Academy: This is your go-to. Learn about SQL injection, Cross-Site Scripting (XSS), and more, with hands-on labs that simulate real-world vulnerabilities.
- Know How to Read and Manipulate HTTP Requests: Tools like Burp Suite become your best friends here. Practice intercepting, modifying, and replaying HTTP requests to see how applications respond. This is invaluable for bypassing simple security measures.
Cloud Penetration Testing ☁️
With cloud services expanding rapidly, understanding cloud environments is essential:
- AWS Knowledge: AWS remains dominant in the industry. Tools like Pacu and AWSGoat help you practice with cloud-native attacks. You’ll learn to identify open S3 buckets, misconfigured IAM roles, and privilege escalation paths within cloud services.
- Practice on Labs: PwnedLabs offers a variety of scenarios that simulate real cloud misconfigurations.
Learning by Doing: Lab Environments and Simulations 🏗️
1. Set Up Your Own Labs
- Virtualized Networks: Build home labs with hypervisors like VirtualBox or VMware. Use a mix of VMs to simulate network topologies and test various attack vectors. Practice creating scenarios with misconfigured services, weak credentials, and exposed network shares.
- Virtual Network Adapters: Knowing how to configure and troubleshoot different network adapter types (e.g., NAT, Bridged, Host-only) in your hypervisor saves you a ton of headaches when setting up complex labs.
2. Vulnerable Machines
- VulnHub and TryHackMe: These platforms provide downloadable VMs and web-based labs, respectively, that cater to different skill levels.
- Hack The Box (HTB): Though often tougher, HTB challenges push your skills further. The community is also a treasure trove of hints, walk-throughs, and explanations.
Expand Your Skillset: Beyond the Red Team 👨💻👩💻
Penetration testers often benefit from a bit of blue-team insight:
- Defensive Knowledge Improves Offensive Skills: Understanding how blue teams detect and respond helps you craft stealthier and more effective attacks. Learn basics about SIEMs, EDRs, and how alerts are triggered. This insight helps you avoid noisy techniques during engagements(Learn about OPSEC).
- Incident Response Practices: Familiarizing yourself with how SOC teams handle incidents can teach you how to make post-exploitation more difficult for defenders.
Additional Wisdom for the Path 🚀
1. Stay Curious and Adapt
- Cybersecurity evolves quickly. Keep up by following researchers, participating in online challenges, and attending conferences (even virtually). Blogs, forums(from China, Russia, Germany and some other countries) like Reddit’s r/netsec, and Twitter accounts of industry experts are goldmines of current trends.
2. Team Up and Network
- Join cybersecurity groups and forums. Collaboration with peers exposes you to different approaches and helps you grow faster. Community-driven platforms like Discord, CybSec communities, and local CTF teams can be invaluable.
3. Embrace the Mental Game
- Pentesting isn’t just technical—it’s a mental puzzle. Sticking with a challenging box or a tough code analysis builds the resilience needed for real engagements. When frustrated, step back, take a breather, and return with fresh eyes. That’s often when breakthroughs happen.
Conclusion: Keep Breaking to Keep Building 🏆
At the core of penetration testing is the relentless drive to understand how everything fits together, break it, and learn from it. From initial curiosity sparked by TCM Academy to going beyond by learning how things are built, remember: mastering the basics gives you the power to tackle complex challenges. Every command line typed, every exploit researched, and every lab conquered adds another layer to your expertise.
Stay curious, stay ethical, and remember: Hack to learn, don’t learn to hack.
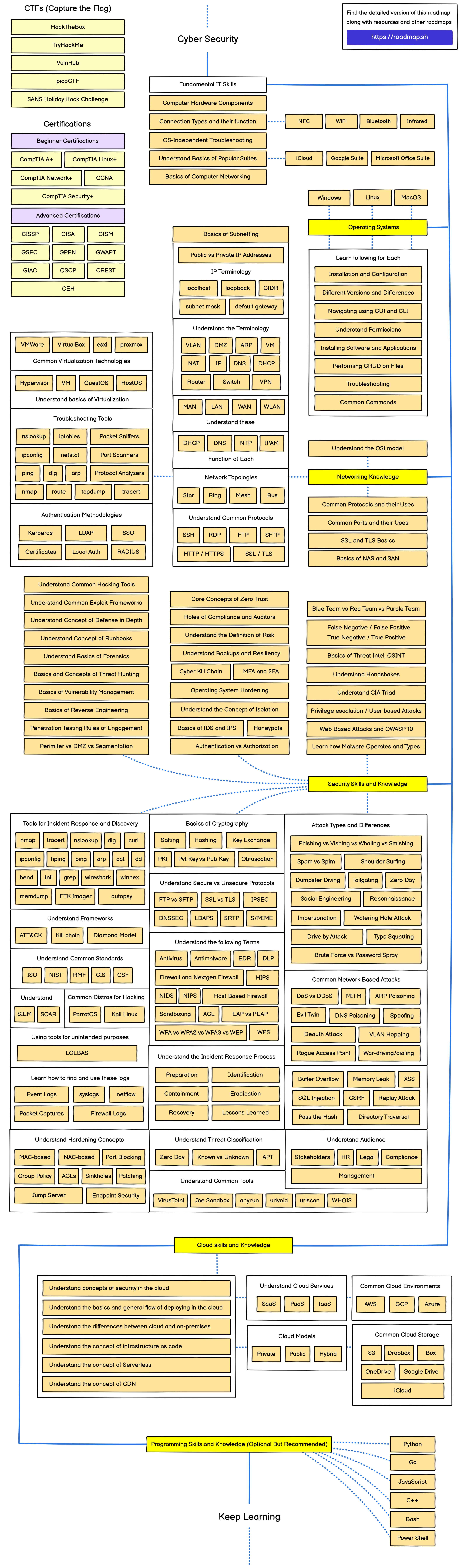 Above roadmap is from roadmap.sh. Don’t follow this certification path, know what you want to do before doing certification(Look at certification reviews and their table of content before taking them)
Above roadmap is from roadmap.sh. Don’t follow this certification path, know what you want to do before doing certification(Look at certification reviews and their table of content before taking them)
Happy hacking! 💡👾
Above blog is generated with the help of GPT XD